A multinational enterprise, managing a large-scale Microsoft 365 (M365) and Azure environment across multiple regions, required a solution to:
- Analyze large number of high severity security alerts.
- Reduce operational costs of security analysts dealing with recurring security alerts.
- Standardize recommendations for security alerts resolutions.
- Strengthen security across cloud resources and identities.
- Control and optimize costs across subscriptions and tenants.
- Ensure governance and compliance with internal and regulatory standards.
- Maintain data localization to comply with regional privacy laws.
They wanted an AI-driven automation engine to continuously analyse their environments and provide actionable recommendations and automated remediation where possible.
To design and implement an AI-powered, cloud-native recommendation engine that continuously analyses Microsoft 365 and Azure infrastructure environments and provides actionable, context-aware insights focused on:
- Enhancing cloud security posture through proactive misconfiguration detection.
- Use Artificial Intelligence to reduce triage time and analyst fatigue
- Standardize resolution recommendations by using Microsoft official documentation.
- Ensuring governance and regulatory compliance by mapping current configurations against policies.
- Enforcing data localization requirements across global cloud deployments.
- Empowering stakeholders with real-time recommendations and visualizations through a responsive Angular frontend and interactive dashboards.
The ultimate objective was to reduce manual overhead, increase operational efficiency, standardize response and to enable intelligent decision-making at scale using generative AI, vector search, and cloud services.
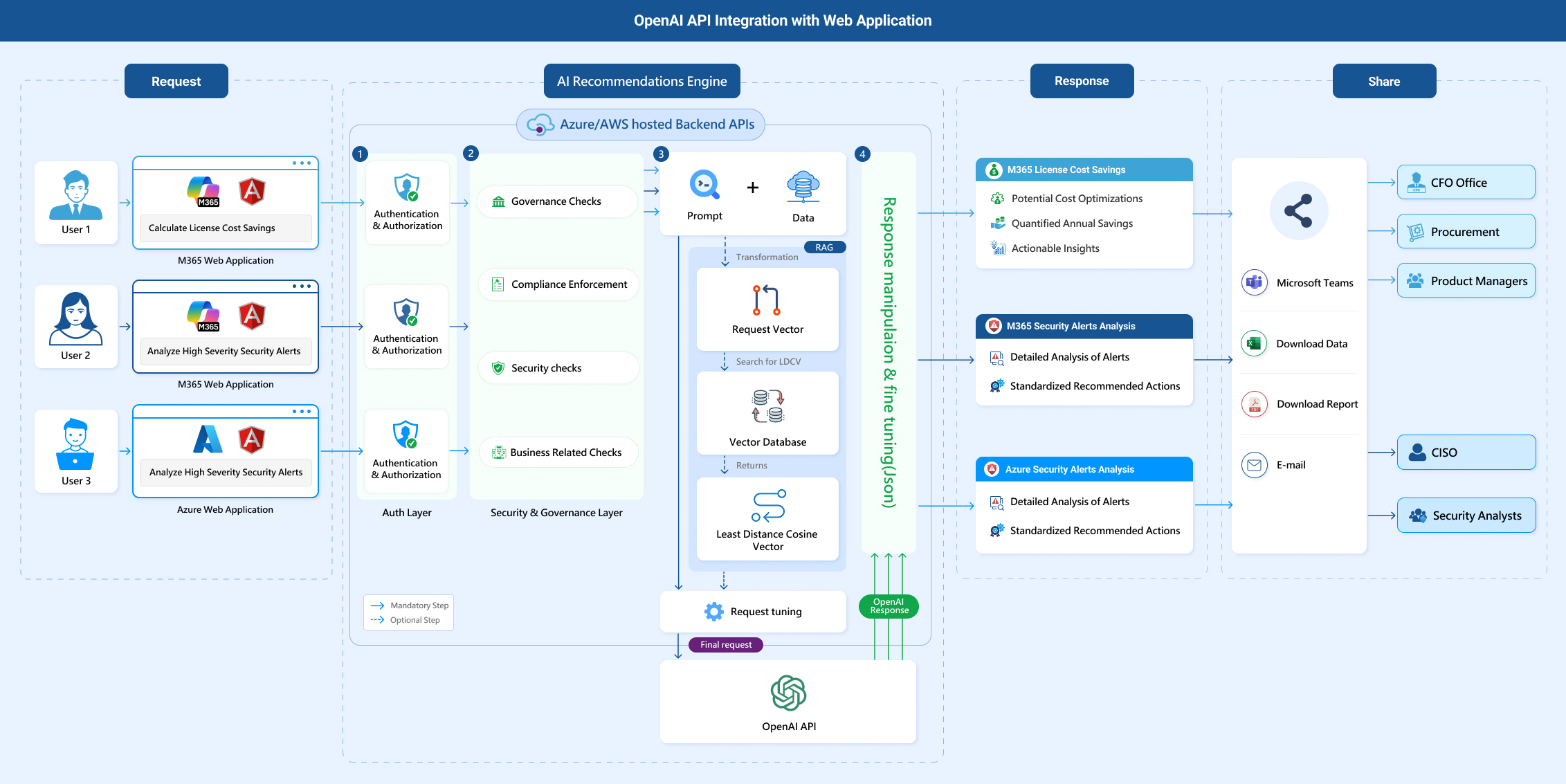
Loves Cloud designed and implemented a GenAI-powered, cloud-native recommendation engine that integrates the OpenAI API with the client’s Microsoft Azure and Microsoft 365 management platform.
Key Capabilities:
- Alert Ingestion & Classification: High Severity Security Alerts were pulled from Microsoft 365 Defender and Graph Security API and enriched with metadata (e.g., user, device, location, alert history).
- Prompt Engineering: Custom prompts were dynamically created for each alert category (e.g., suspicious inbox rule, privilege escalation, malware activity) to elicit tailored responses from GPT-4.
- Generative AI Integration: The OpenAI API was queried to generate human-readable summaries, impact of the alert and context-aware recommended actions based on each alert’s metadata (e.g., alert type, user, device, location, alert occurrence).
- Integration into Analyst Workflow: The AI-generated response was embedded directly into the existing security alerts dashboard, allowing analysts to review it and share with more stakeholders through inbuilt Microsoft Teams Integration.
- Consistent, Timely and Accurate Analysis: The OpenAI API uses Microsoft’s official documentation to query data for security alerts, thus ensuring that all information is consistent and accurate, instead of relying solely on analyst’s experience.
This solution used following tools, platforms and services:
- Artificial Intelligence & NLP (Natural Language Processing)
- OpenAI GPT-4 / Azure OpenAI
- RAG (Retrieval-Augmented Generation)
- Vector Databases
- Pinecone / Azure AI Search (Vector Indexing)
- Backend
- C#
- Frontend
- Angular (v15+) – Modern SPA frontend with modular UI components
- Power BI – Embedded dashboards for all stakeholders
- Cloud Platform
- Azure – Azure OpenAI Services, Azure Monitor, Log Analytics, BLOB
- AWS – S3, CloudFront, Route53, Amazon Bedrock (optional)

Following are direct and major results of implementing AI-powered recommendation engine:
- Automated triage ensured 100% visibility into high-severity events.
- Analysts focused only on escalated or ambiguous alerts, reducing alerts fatigue.
- AI recommendations aligned with Microsoft’s security best practices, resulting in improved compliance readiness.
- AI-generated steps aligned with internal SOPs and security policies, resulting in standardized playbooks.
- Integration acts as a reusable foundation for future use cases (e.g., insider risk, phishing triage, sign-in denied users analysis etc.).
Additionally, following Key Performance Indicators (KPIs) improved significantly as a result this AI recommendation engine implementation:
| KPI | Baseline (Before) | After Implementation | Impact |
| Security Misconfigurations Detected | Manual, Ad hoc | 90% Auto-flagged | 🔐 Increased threat visibility |
| Cloud Cost Savings | – | 22% Reduction in Q1 | 💰 Lower operational cost |
| Policy Compliance Coverage | ~70% | 98.5% | 📋 Stronger governance enforcement |
| Remediation Turnaround Time | Avg. 2 weeks | < 24 hours (automated) | ⚡ Rapid response time |
| Data Residency Violations | Unknown | 100% Detected & Resolved | 🌐 Full localization compliance |
| Engineer Time Spent on Reviews | 40+ hrs/month | < 5 hrs/month | 👨💻 Massive productivity gain |
| Recommendation Accuracy (measured via feedback loop) | N/A | ~92% relevance | 🧠 High trust in AI insights |
Want to enhance your Microsoft 365 and Azure security alerts workflow with GenAI?
📩 Reach out to Loves Cloud at biz@loves.cloud to get started today.